XMPP Federation
XMPP Federation enables users exchanging chat messages and presence information with external users accross enterprise network boundaries.
A detailed description of federations can be found on the Introduction to Federations page. Step-by-step instructions for creating an XMPP federation can be found on the Creating an XMPP Federation page.
Using XMPP Federation
Check the Use XMPP Federation checkbox to activate XMPP Federation.
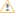
|
In order to enable the estos UCServer to contact a domain through XMPP, a corresponding domain authorization with a public business, team member or personal authorization level is required. The protocol type must be set to "XMPP". Domain authorizations for popular XMPP domains (such as gmail.com) were configured as part of the estos UCServer installation process. |
Determine how the connection to other servers should be created:
-
Direct
The connection to servers in other XMPP presence domains should be direct from this server. An XMPP server-to-server interface will be opened to allow other servers to connect to estos UCServer:
-
TCP Port
Enter the TCP port for the XMPP server-to-server interface. The default port, 5269, can be set by clicking the Default button. -
Bind to IP address
Select an IP address for your system, through which the XMPP server-to-server interface should connect.
Make sure that this interface can be reached through the public Internet and that your presence domain can be resolved to an IP address by DNS. If you configure a different port than the default, a DNS SRV Record (_xmpp-server._tcp.domain) can inform other systems about this. Ideally, such a DNS SRV Record should also exist, when the default port is used. However, this DNS SRV Record is not mandatory, since other systems can also generally connect to your estos UCServer using a DNS A Record and the default port, 5269.
The certificate used for server-to-server connections as well as other options for encrypting the connection can be set by means of the "Advanced..." button. However, only the connection to the XMPP server in those domains, which encrypt messages and forward them to remote users, will be encrypted. End-to-end encryption is not used.
A server certificate will be required for using the secured TLS and MTLS network protocols. The certificate must have been signed by a certification authority. Click the Certificate button to open the window for selecting a certificate. Select the appropriate certificate and confirm it by clicking the OK button. Information about the selected server certificate will also be displayed. If you do not specify a certificate, but a SIP server certificate exists, an attempt will be made to use that certificate.
The settings for TLS encryption may either be set globally for all domains or locally for each individual domain. The global settings will apply for all domains, when other settings have not been made. In order of accessibility and trustworthiness, the following categories can be assigned:-
Keine Verschlüsselung
TLS encryption will not be used for connections with remote domains. This setting should only be selected when the TLS Encryption Optional setting will not work.
-
TLS Verschlüsselung optional
An attempt will be made to use TLS encryption with connections to remote domains, if that domain makes such possible and a local certificate is available. If the other domain does not offer TLS support (which is the case with GoogleTalk, for example) then message exchanges will not be encrypted. Otherwise, the attempt will be made to ensure the highest possible level of reliability. This settings will almost always work, but does not guarantee the reliability of the messages.
-
TLS Verschlüsselung erforderlich, Zertifikatfehler ignorieren
The attempt will be made to use TLS encryption with connections to remote domains. If a local certificate is not available or the other domain does not support TLS, the connection will fail. If certificate errors occur (for example, because the other domain's certificate has expired or has not been signed by a reliable certification authority), they will be ignored. Connections will offer reliability, however not strong authentication in the other domain.
-
TLS Verschlüsselung mit gültigem Zertifikat
The attempt will be made to use TLS encryption with the connections to remote domains. If a local certificate is not available, the other domain does not support TLS or the other domain's certificate is either invalid or not signed by a reliable certification authority then the connection will fail. This type of encryption is recommeneded, does not however always work (for example, GoogleTalk does not support TLS encryption, many server certificates have expired or they have only been signed by the server itself).
-
-
XMPP Proxy
The connection to servers in other XMPP presence domains will be made through estos XMPP Proxy.
-
Proxy TCP Port
Enter the TCP port to which estos UCServer will connect the estos XMPP Proxy. The port can be set to the default port, 5275, for the proxy connection by clicking the Default button. -
Proxy Address
Enter the address for estos XMPP Proxy. -
Passwort
Specify a password, which estos UCServer should use for logging onto estos XMPP Proxy.
-
Version 8.3